.
Everyone carefree
and safe at work
This is Workplace Management
The management, maintenance and security of all IT in your workplace/office is part of your company's management. So, for example, your pc or laptop, a docking station, a (VoIP) telephone and so on. These all need to be managed, i.e. secured, updated, monitored and supported by a professional helpdesk.
Is a workplace all about a nice chair, a picture of your family and a cactus? Not at all! You just want to be able to work carefree without being constantly interrupted by technology. Every day!

Safe and sound at work
without interruptions
Your PC or laptop with all the services around it should contribute to your performance. Every day. We can take care of that for you with Workplace Management. Everything needs to be set up, managed and monitored. So you and your colleagues can perform and do what you do best without distractions and annoying malfunctions. Workplace management just makes you and IT work!
We take complete care of IT and you, have a passion for technology and can communicate clearly about it. We are proactive, advisory and let you and the technology lead the way. If you need help or if things go wrong, one of our specialists will help you quickly and competently.
Part of Managed IT
A workplace is more than a desk with a cactus and a picture frame.
Workplace management provides peace, security, continuity and a lot of happiness.
That's why you need Workplace Management
This is how we help you optimally
Advisory role
We go one step further. We also take an advisory role, giving you personalised advice. Which laptop is right for you, is a docking station perhaps a good choice and which screens do you need? It's all about IT and your business.
Available on a monthly basis
Like all our services, Managed Workspace can be cancelled monthly and you pay according to use, giving you flexibility. It's no problem if your business grows or shrinks.
Acting proactively
Sometimes we solve problems long before you even realise there is a problem. Because we make IT simple and have experience, we know the solution to most problems straight away. For difficult problems, you can rely on one of our professionals and get the most out of the benefits, without the problems.

Does it go wrong? Then we are here for you!
010-2121806 - helpdesk@limenetworks.nl
Frequently asked questions about Workplace Management
In fact, it IS a subscription/contract! That way, you have certainty with agreements such as the SLA (service level agreement) and the nature of the service. We believe in long-term relationships but not in long-term contracts. At Lime Networks all contracts, including Workplace Management, can be cancelled per month.
We do not mention prices on our website. We do have fixed prices for all our customers on our maintenance contracts. How much will it cost for you? Just give us a call and you'll know.
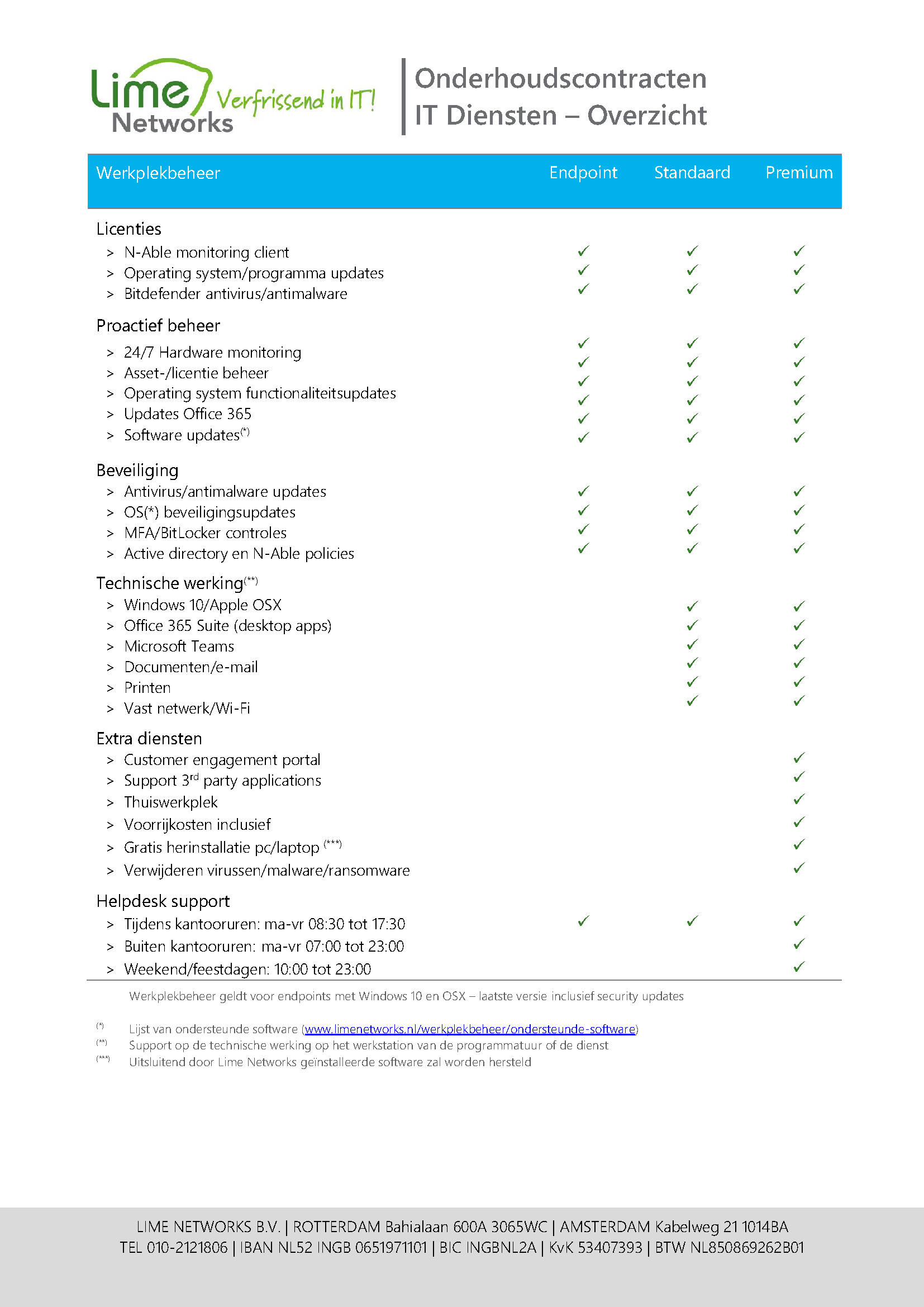
- A piece of software for managing your pc/laptop which also monitors and reports
- In addition, an antivirus/antimalware package
- An update strategy that ensures that all components (hardware, software, security) are up-to-date
- Finally, a full-service helpdesk with passionate IT people who will help you promptly if you encounter problems or if something is not working as it should.
For us, an optimised workplace is one where you can work comfortably and perform optimally for your company. For example, your workplace must function well, be smooth and above all safe so that you are not interrupted. But also, for example, a laptop with a docking station and two screens so that you can do your work more efficiently and enjoy it more.
The management, maintenance and security of all IT in your workplace/office is part of your company's management. So, for example, your pc or laptop, a docking station, a (VoIP) telephone and so on. These all need to be managed, i.e. secured, updated, monitored and supported by a professional helpdesk.
Everyone has their own workstation. Sometimes with a cactus or Bonsai tree, sometimes with an extra screen, a printer, a wireless keyboard, a scanner, connected to Wi-Fi, a docking station, a (VoIP) telephone and you name it. But the most important thing is your pc or laptop. That is the core of your workplace. So we are not talking about your physical desk, but the IT side of the story.
That you are not working in an unsafe workplace with outdated software, missing updates and inadequate security. Adjustments are made to prevent problems with your workplace. Failures that occur frequently due to the complexity of all components are solved automatically with smart scripts. This keeps your workplace healthy. The only thing you notice is that you experience fewer malfunctions. Finally, the management provides insight into licences and hardware in use and ensures proper monitoring, control and help in solving any malfunctions.
The advantages are that you work safely and that everything works properly. And if something goes wrong, we can help you back on track efficiently. You are important, so is your workplace. Apart from this, we know that you are up-to-date with all your software and security (antivirus/antimalware). You have all updates for your hardware and software, so everything works optimally. We also have clear reports on the health of your workplace and can easily manage it. For support, you don't have to wait for someone to drop by, because we are well informed and can help you remotely straight away. With a good SLA (service level agreement), you can be sure that you will be helped quickly.
Basically all the hardware you need for your workplace. A pc or laptop possibly with a docking station and optionally a monitor, printer, phone or other things that you need to do your job well.
If you have a second pc or laptop, we secure this endpoint just as well as the first. Your helpdesk contract also applies to this endpoint and the aim is to work in exactly the same way in both places wherever possible.
With Office 365, your company network and/or back-up software, we ensure that you do not lose any data - not even in the event of defects, theft or loss of hardware. It's all about you being able to do your work efficiently and with peace of mind.
We would love to be able to tell you that a virus does not exist at all, but unfortunately there are many examples of this happening. We won't let you down on this! We will make sure that we measure and analyse the problem (for your ISO reporting or insurance, for example). In addition, we ensure that you can quickly get back to work without any loss of data. Sometimes this is done in the blink of an eye, sometimes we have to reinstall your pc. Whatever the case, we are there for you and will help you quickly.
In a nutshell, we provide a safe, high-performance workplace for the long term. In addition, we help you immediately if something is not working so that you can continue your work as soon as possible. Because nothing is as annoying as not being able to do your job!
Yes, we do! Do you have your own helpdesk or do you have some knowledge in house? Then start with endpoint support or call us if your IT person is on holiday, unavailable or ill. Are you short of hands or do you want to start a big project? We help you wherever you want, just as easily. Sometimes it is also very useful to hire some ready knowledge on subjects you are less strong in.
You call our help desk. Even outside office hours if you have an agreement to do so. The helpdesk helps you directly where it can and informs you by e-mail about all steps. With a good registration in 'tickets' you can also look back later.
Don't worry, don't panic. Your data is safe. With Bitlocker and our security policies, no one can get to the data, even if you disassemble the laptop. If your pc is connected to the internet, we can still wipe it clean. We immediately make sure that you can get to work on a loan laptop from your company or perhaps another workplace. Sometimes you can even access everything via the Internet at any workstation or at home. The delivery of a new pc or laptop is immediately arranged, so you will soon have the comfort of your own workplace again.
It is not as difficult and inconvenient as you might think! We ensure that you get a working pc or laptop in your office that is properly installed with software, updates, security, management and all the specific software and settings for your company and/or function. No messing around with settings and programmes or registering programmes or removing unnecessary software. We transfer your settings at the office so that you can start working immediately and safely.
To achieve safety, performance and continuity. Everyone wants to be able to do their work safely everywhere. Everything must function properly, despite all the problems with hardware and software, the challenges of security and all the software on your pc.
An endpoint is a pc or laptop that your company uses in the company network. This can be a computer behind a desk connected to a presentation screen, but also a computer in a meeting room or belonging to a temporary employee. They all need to be managed, secured and supported.
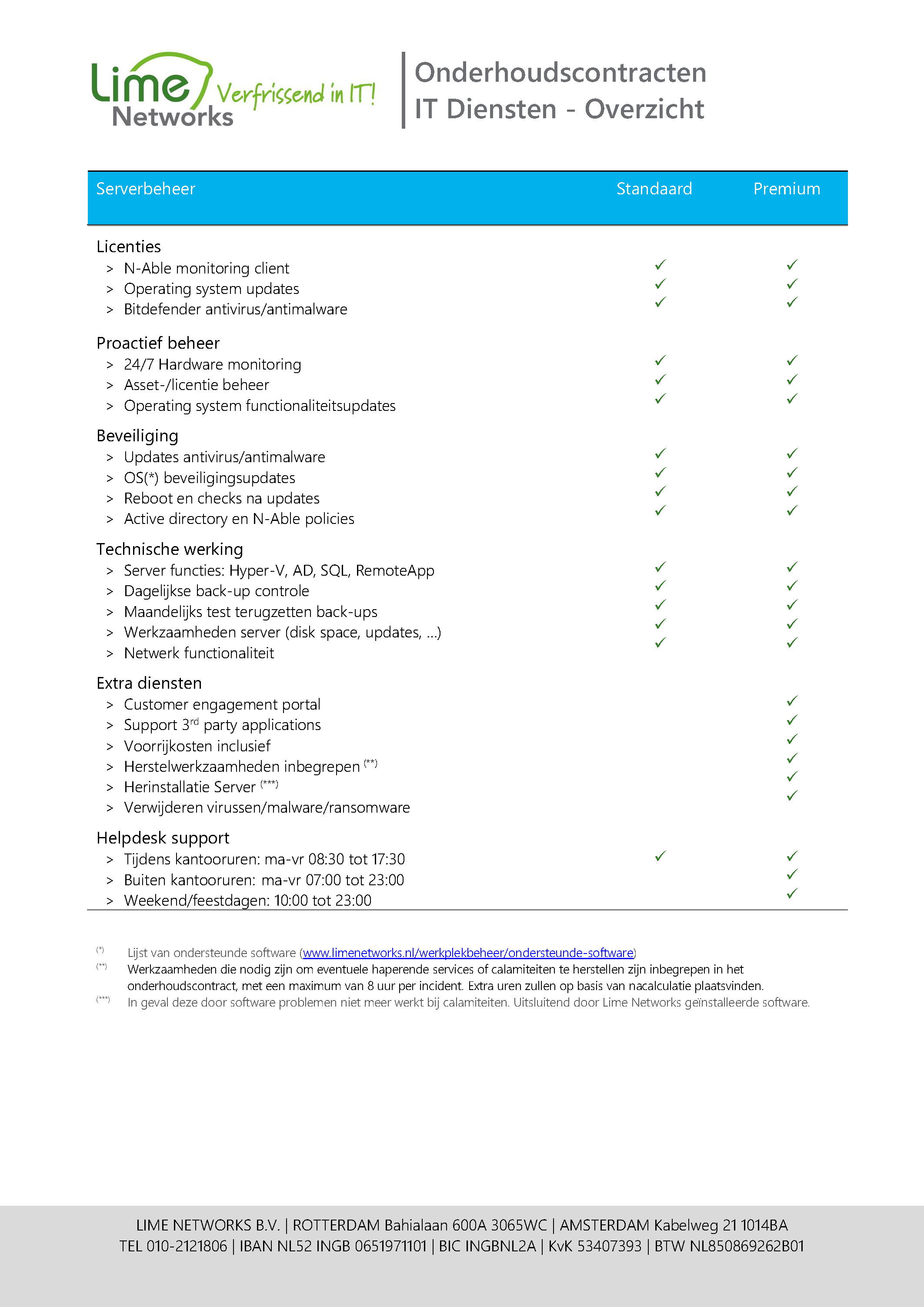
- Records of hardware, licences, warranty, age and so on and who uses the computer
- Security with Bitlocker, antivirus/antimalware or EDR software, security policies, OS security updates and security updates of 1,000+ programs
- Updates of the OS, of 1,000+ programs, of the antivirus/antimalware or EDR program, of drivers
- Management with NAble. For example, we take care of active management of the pc and all settings so that we can (measurably!) make and keep your workplace operational. Also a good control for all measures we take with reporting
- Automation that can prevent more than 50% of all PC problems. Even when things go wrong, many problems can be solved automatically. For example, restarting a jammed process, repairing your search index, cleaning up the pc or automatically repairing log messages.
Terminology difficult? We make it simple for you
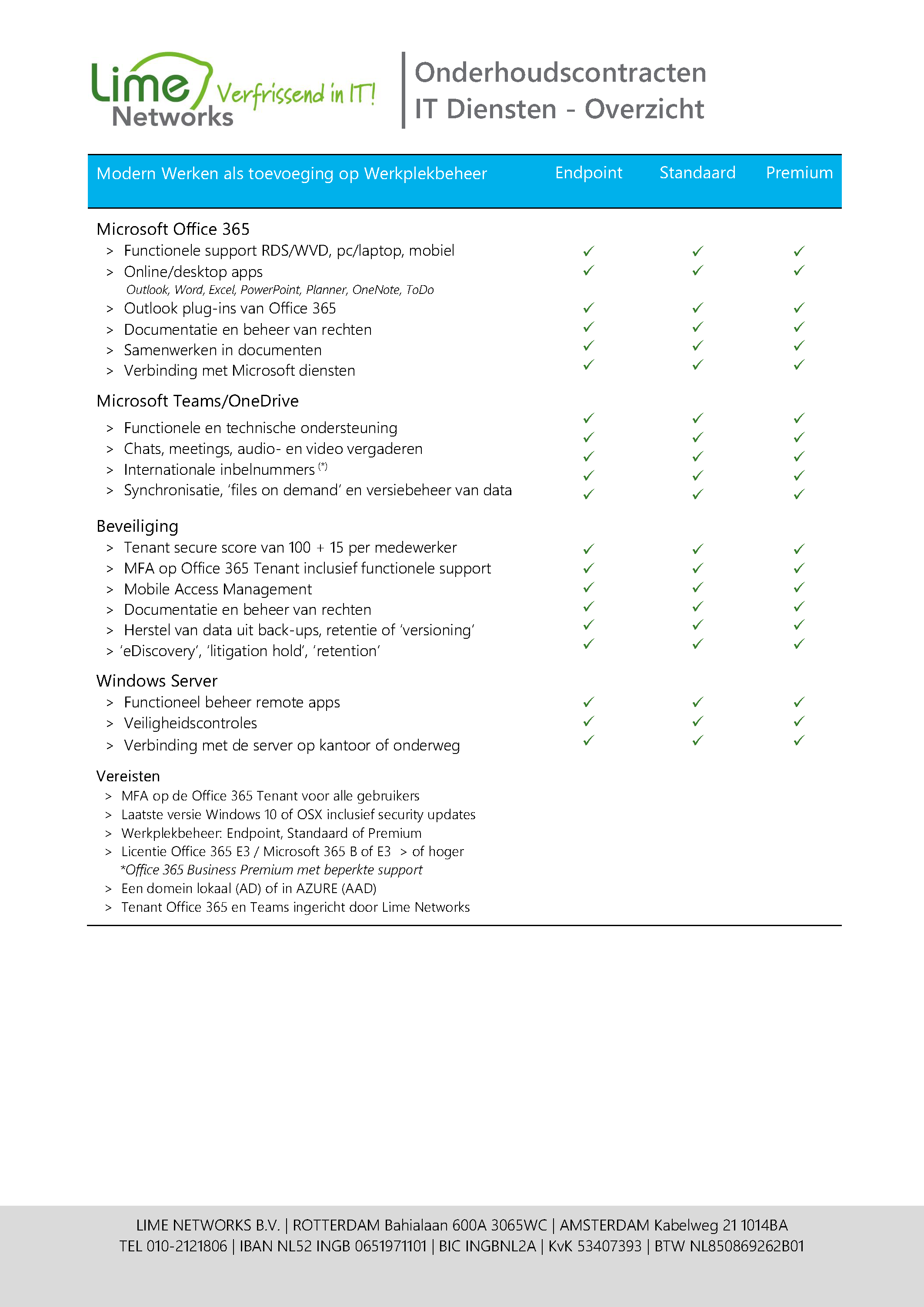
A container in which all your online services from Microsoft are stored. Does your company use a cloud service from Microsoft, such as Office 365? Then space is made available in the Windows Azure data centre for all online services. With Windows Azure Active Directory (WAAD) you can manage your users. Create a link to the Active Directory at your own location via Active Directory Federation Services (ADFS). When activating these online services, customers often think that the tenant is only the domain of the Office 365 users, but this is actually only the case if you do not specify your own domain.
A score for how secure the tenant is set up for you, judged by Microsoft. They also compare the security interface with other companies to see how high you score. You want to score as high as possible on this. The scale runs from 0 to somewhere in the 300s. The average international score is below 25, but we always try to get our clients to score 100+.
A remote monitoring and management tool for IT endpoints (pcs, laptops, servers). We use it to configure, secure, patch, update, troubleshoot, inform, monitor and organise services. There is a possibility for extensive automation through scripting. We use this service for all endpoints under our management.
Retaining email deleted from corporate accounts for purposes such as litigation. Suppose an employee intentionally deletes all emails from one customer, then with litigation hold you can retrieve it and see when it was deleted. Used mainly for litigation and court cases.
Ensures that you receive a warning or block if you send a message with privacy-sensitive information such as your social security or credit card number. You are then asked if you are sure you want to send that information, so that your data is not lost. This works for e-mails but also in Word files.
Possibility to retrieve e-mails, files and calendar appointments from a backup. So not the whole mailbox but really specific search on keywords, sender, date, etc. What you can also see: the time of deletion and reason for deletion (e.g. if a process is running, such as the automatic archiving of files that are 10 years old).
Extract e-mails or files from normal location and place them in an archive. Set, for example, that files older than 3 years are automatically moved to the archive. In this way you can optimise e-mails and files, for example if you are looking for a file from a certain year.
One large file stored at Microsoft for 90 days, in which every action is logged. This can be read online by administrators. For example, you can see who called who, when and what actions were taken. The function: transparency and honesty; we cannot do anything without the customer knowing it.
Retention; storing, managing and editing files within a certain policy. For example, a rule such as 'all files belonging to Lime Networks are deleted every year'. Or 'all tax data cannot be deleted for 7 years' or 'we can retrieve files for up to 10 years' or 'we are going to allow edits for 30 days and after that 30 day creation no one is allowed to edit any more'. The sky is the limit! So it is all about setting.
The umbrella term for everything that can be encountered by malicious persons via e-mail and the Internet, such as viruses and phishing. Actually, it is a spam filter, antivirus solution and antimalware. Office 365 has a low default rating that we always increase to ensure and guarantee your security.
We distinguish between two Active Directories (AD), namely a regular AD and an Asher AD. The normal Active Directory is a server in your office where all the users are stored. Think of it as a huge spreadsheet/database where all the usernames and passwords are stored. Of course, this is handled with the utmost security and everything is extremely well protected. The Asher AD is about the same as the regular AD, but then in the environment of Office 365. Microsoft sometimes uses the term 'Identity Management'.
Manage your company's security policies on mobile devices such as smartphones and tablets. These include mandatory MFA, a PIN number for unlocking, your fingerprint or a camera scan of your face (FaceID).