Who says network, says security. Just enter your e-mail address at https://haveibeenpwned.com/ to find out how many times your data has been leaked. Shocking? So this is not what you want with your office network, you want to prevent it. Because we want to make IT simple, we will limit the number of technical terms, but explain at length when there is no better word. Here are six ways to secure your network.
#1: Make use of a firewall
A firewall is a piece of hardware containing software you put on site, which ensures that incoming and outgoing traffic is monitored. Think of it as a kind of box that acts as the ears and eyes of your Internet traffic. This ensures that outside people cannot get into your network without permission. Also if you want to measure on your network or Internet traffic then your firewall can assist in this to gain insight.
#2: Set up 802.1X network security
An 802.1X describes how your device is allowed to connect to a network. You create a policy for it where you set that only certain devices are allowed to connect to a network. Does someone not fall within this policy? Then that person cannot use the company network, but can, for example, use it as a guest with limited functionality. So much more secure!
#3: Set up your Wi-Fi properly
Separate the business network from the guest network. For the business network you do not set a password, but work with the 802.1X network security as mentioned in the previous point. For the guest network you do set a password. This way you offer service to your guests or visitors without making your own network less secure.
#4: Ensure timely (automatic) updates.
All devices on your network require updates. In our managed network, we provide the three components firewalls, switches and access points. Firewalls we explained in the first point. Switches connect all the devices in your network with a cable. They also largely control network traffic, keep order and also control a bit of security. Finally, access points (ap's) are the boxes you see hanging from the ceiling or wall that provide wireless networking. Updates ensure that you reduce the risk of people from outside your office wirelessly accessing your network. Even though you have such a secure network, with a leak on your wireless network, your network is open to uninvited "guests.
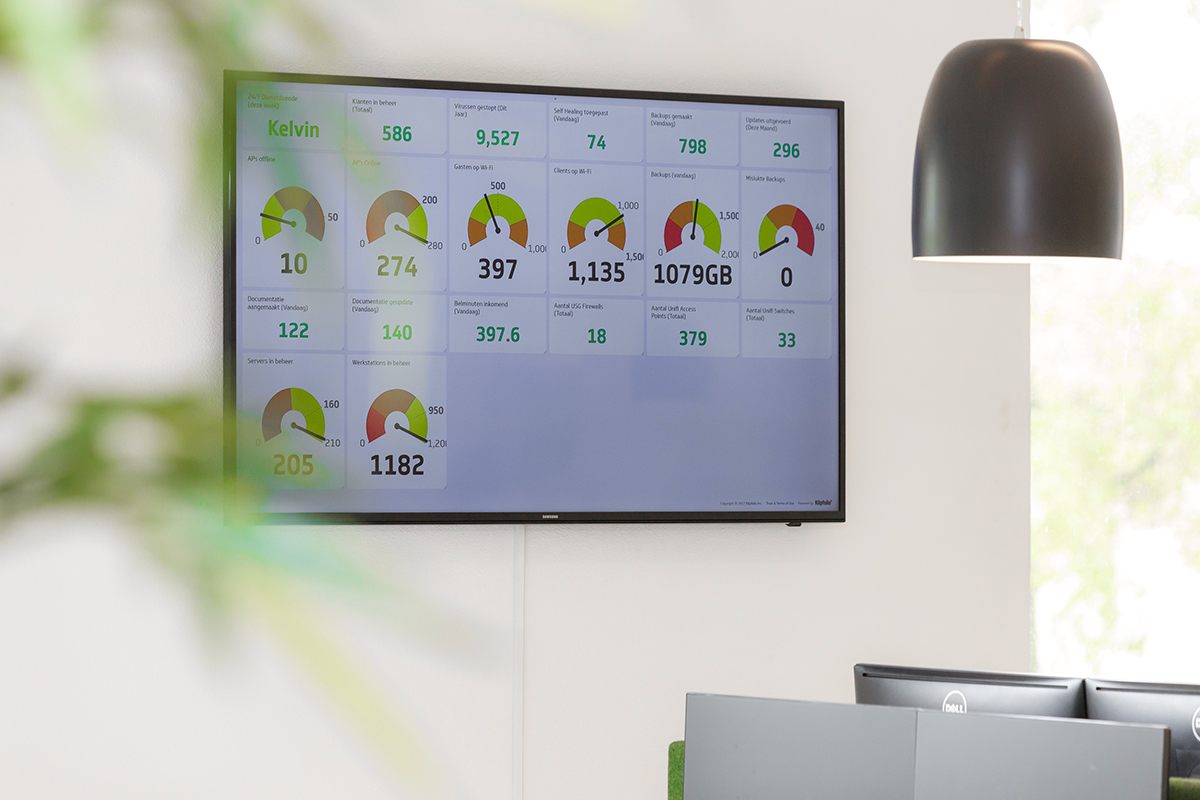
#5: Provide a clear dashboard
Monitoring is key. By this we mean: make sure you have insight into what is happening on your network. A clear dashboard shows what is important to you. For example: who is connected? What traffic is going through your network? What is the quality of connected devices? Are you under attack or is there suspicious traffic on the network? Gain live insight into your network to make your network more secure.
#6: Do a periodic pen test
A pen test is designed to periodically check the security of your network. Someone purposely breaks into your network to check the security and checks all aspects of access to security on your network, just as a malicious person would. However, it is someone with permission by right and thorough training to be allowed to do this, so your data still remains secure. We recommend doing it yourself twice a year and once every two years by an external party to be absolutely sure. You can also include the security of your other IT and/or staff right away. Just as safe.
Are you now thinking, "I don't feel like doing that at all, setting all those things"? Then we have good news for you, because we do feel like it. Very much so. With a passion for technology, we like to work for you and make it simple for your business. Call us on 010-2121806 or e-mail us at info@limenetworks.nl. Our customers can always contact our helpdesk for questions about security, your network, internet or other IT issues.
Frequently asked questions about Managed Network
Is your question not listed? 1 email or 1 phone call is enough to get it answered. 010-2121806 | info@limenetworks.nl
First of all, we make sure that your network is measurable and understandable. Then we can guarantee availability for both employees and guests, separated by service. We then take care of access management and secure the network against uninvited guests. Do you have requirements for DNS management, additional firewall settings or a VPN to other offices, the cloud or a data centre? Then we monitor the correct operation for you. Optionally, we can monitor all data traffic on your network with a third-party service so that you can be absolutely sure what is happening on your network.
A wireless network is not about megabits or technical terms. It is about much more than that. A Wi-Fi network is already slower than a wired network, but if you have many users you need to plan, measure and estimate your usage in advance. If you have several floors or offices with many walls and/or furniture, it is good to have experience in this. If you have a warehouse with a lot of shelving, that's when it gets really tricky. We make sure that all the technology is really effective and comfortable to work with. Leave the technology, the measuring and the setting up of the cooperation to us. We make it easy for you.
A fixed network is like a fuse box with groups; it is not one entity, but it is almost always segmented in order to channel all data. It is not a matter of plugging in cables and that's it. Planning and control are necessary to make everything work properly. You do that with VLANS, QoS, Spanning Tree etc; not so simple. Monitoring data for security and detecting possible problems is also essential if you have problems. Also, if things go wrong with connected devices, cables or defective equipment, you need to have insight so you can react quickly. To gain this insight, you must be able to see live usage and all settings. And not just over a single device but over the entire network. So it is really complex if you want to do it right.
At Lime Networks we hate cable slack. When we arrange your network it is not spaghetti but as fresh and fruity as can be. A well laid out network prevents (unintended) disruptions and shortens the time needed to solve problems with changes and defects. Since you pay per month, we want this too 😉
With every new customer and/or project, we always make a plan of approach first. A thorough inventory on site and the elaboration of all facets (preparation, installation, configuration) including the impact on your company and employees are clearly described herein. We only start work if you agree to it. So it is clear what we do, when and why. This should prevent your company from having difficulty making the switch.
No, like almost all services of Lime Networks you pay per month. So you are not stuck with anything. Even if your company needs a different solution we will help you with a smooth transition including documentation, advice and helpdesk.
Through monthly contracts, we ensure timely expansion of your network. Without complex discussions. A '+' for the number of access points, for example, and we take care of the rest. In the event of a decline, you can always opt to terminate part of the contract free of charge; per device, in other words. That way, you always continue to pay for your use and are not tied down to anything.
No, unfortunately. There are firewalls that have some form of data control. However, this is a limited part of your data. A lot of data moves around your network securely or is not visible to smart firewalls. The best remedy for keeping these forms of cybercrime at bay is not in your network but in the security of endpoints, data, users, servers etc. Up-to-date endpoints, antivirus (or even better EDR), encryption, a good password policy, a solid rights structure on your data, MFA on all your external software and/or services do provide more security. The final benefit lies in your staff, who you can train in security awareness. Prevention can never be 100% guaranteed, but if things do go wrong, we will be there for you. We will help you to get back up and running quickly.
Within your network, we make certain data flows transparent and can separate outsiders (guests) from your office network. The correct security settings prevent uninvited guests from gaining access. Your data can thus move safely across the network without restrictions or prying eyes.
By using IPS/IDS, you have a good basis for working unwanted things off your network and making your data flows on your network transparent with measurement. This is part of the standard services.
To create secure connections to your network, cloud service or data centre, we provide solutions for optimal connectivity. We handle the technology; sometimes in combination with your IT department, supplier or external service provider.
We work together with all internet providers and all services on them. Sometimes with the intervention of additional equipment from your supplier such as modems or routers. As far as we can see, there are no restrictions.
Speed on networks can sometimes be complex. If performance is not as it should be, we always start by measuring it. After gaining insight into possible bottlenecks, we provide a quick remedy to get your network performing optimally again. Whether this concerns settings for VLANs and QoS, expansion of capacity due to growth, faulty equipment or measuring the Wi-Fi again. Your company gets a solution, POINT. So you don't have to worry about that.
With our cloud controllers, each branch office of your company gets its own controller for the network. With a central management for security, updates, monitoring and configuration, all components can be closely monitored and measured. In the event of a failure, notifications are automatically generated in our management systems and engineers automatically set to work to ensure the optimal performance of your network.
Yes, we do! Because everything is well documented and all components are in stock, we can get straight to work without any questions asked. This shortens service times considerably.
We usually notice this before you do and immediately proceed to replace the defective component. The hardware, replacement, travel expenses, man-hours, installation, configuration and warranty settlement are included in the service. A good SLA ensures that you can quickly work again on a problem-free network.
Not separate or apart. It is silly to say that you do not pay for this. Of course, it is included in the price. The hardware, the installation, the management, the security, the fault handling... we offer all this for a fixed amount per month per network device. So you don't pay this in advance, but it is part of the monthly contracts. This ensures predictable costs.
Experience is where you get the most benefit. We have knowledge of our products, so you can benefit from the experience of a large group. If you do have questions, our full-service help desk is ready to help. Your documentation, network and monitoring will be readily available so you can be helped quickly. And if any hardware fails, we'll be there quickly with replacement hardware. Settings are ready in the cloud so there is virtually no installation time. Afterwards, we give you insight into your network and advice on how to make it even better. Top service!
Of course, we support all known techniques for controlling and securing your network and the data sent over it. This is included in our standard service, even if you sometimes have changes.
Just like a mobile phone, you can buy it yourself and buy a prepaid subscription. Great solution. You don't have to do anything. Do you want to keep it simple, make costs predictable and outsource the responsibility to professionals? Then we think that is a wise choice for the business. That way, you can shift your attention to things that make a difference or in which you can compete with your sector colleagues.
Do you still have a good firewall or wireless network managed by another party? If so, feel free to continue using them. Mixing different products within the components (fixed or Wi-Fi) is not desirable, so we do not do that. Do you already have equipment from the same supplier? If so, we will take it over and at the same time take over the responsibility, guarantee handling et cetera.
You pay a fixed amount per component per month - literally for a firewall, a switch and a Wi-Fi point. For this, we provide advice on security, network design and what you need to think about or make choices in. We write a plan of action so you know exactly what is going to happen, by whom, when and what the impact is for your business. We install, secure and test the network. The Wi-Fi is measured in detail with a test report. We maintain and continue to secure the network and monitor it during use; actively with a portal in the cloud. In case of user problems we have a full-service helpdesk and in case of failure we are quickly on location with replacement hardware. Updates for functionality, security and reporting are part of the monthly service. And software licences, updates and additional support are included at our premium level.
A network does not consist only of equipment and cables. Securing your data, the performance of all users on the network and the continuity of your business are essential. We make this simple for you, for a fixed amount per month. We are here to take care of all the tricky stuff without complicated invoices or you having to pay for every change. Simple, safe and taken care of.
A firewall protects your network, but also controls a large part of the data on your network and all the data coming in and going out of the office. This data must be transparent and well protected. Moreover, this data must be prioritised in order to work well together. In addition, you need to make updates to keep security up to date with both the software and the settings. Securing one firewall is quite difficult, because it takes a lot of time. But if, like us, you manage more than a hundred, then it becomes easy.
We see the network as the system that connects computers, printers and other IT equipment in your office to make use of the internet. Think of the firewall, the fixed network and the Wi-Fi network.
According to Wikipedia: "A computer network is a system for communication between two or more computers." The communication is done via network cables or via a wireless network. In network topology, physical and logical topologies are distinguished. One speaks of a LAN in the case of local area cabling to which computers within one building or campus are connected, and a WAN when connections over greater distances are involved.