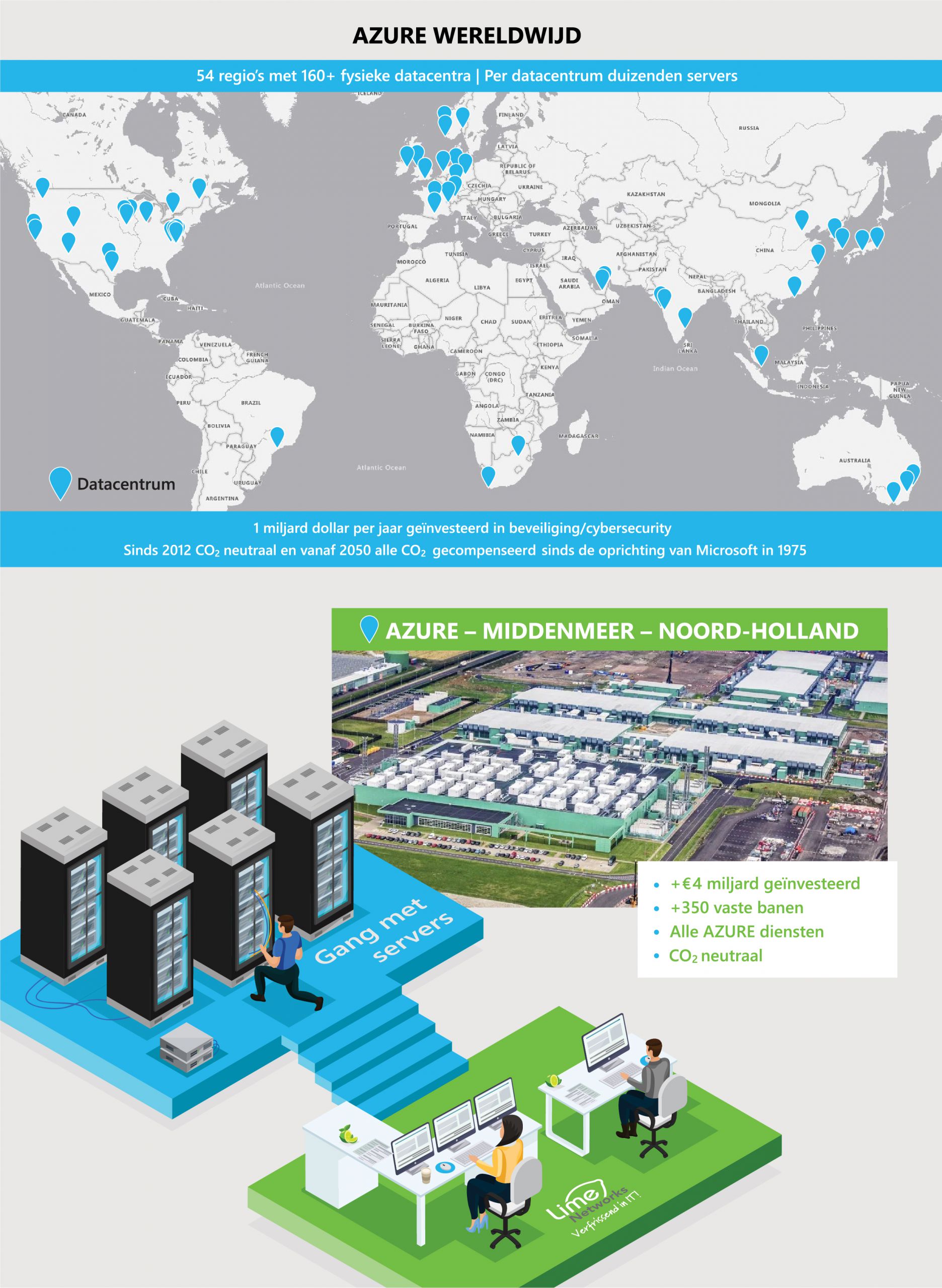
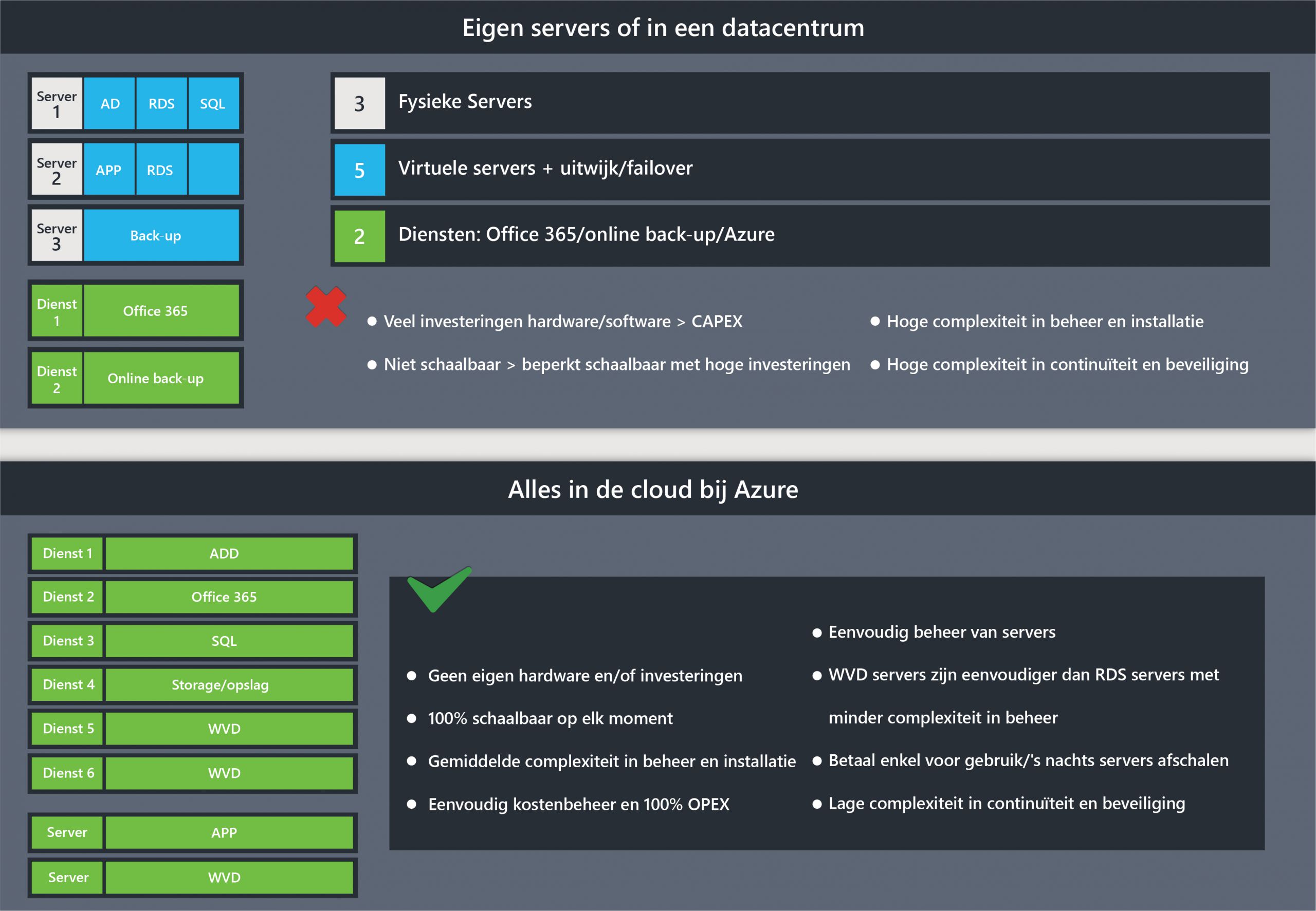
.
The big IT ABC
From Lime Networks
The big IT ABC of Lime Networks
IT is and always will be a complex concept, so are many IT terms. When we find that a customer does not fully understand an IT term, we explain it in simple terms. Because at Lime Networks, we believe that IT should be simple and secure and that customers should be taken care of by passionate people who communicate clearly. Making IT understandable and completely unburdening you as a customer is our goal.
To make things even simpler for you, we've listed the most confusing, misunderstood IT terms by IT service for you! Are you missing any IT terms in the list? Let us know via email!

List the most confusing, misunderstood IT terms by IT service
Managed Network
- Firewall: a firewall protects your network, but also controls much of the data on your network and everything that comes in or goes out of the office in terms of data
- Hardware: anything physical, meaning anything you can put your hands on; firewall, access points, switches, keyboard, phone, laptop, server, firewall. It is something that exists
- Helpdesk: a first point of contact for IT problems or questions about the operation of IT things (software, hardware etc)
- IDS/IPS: Deep Packet Inspection; a way to understand and examine network traffic, giving you a more secure environment. It also allows you to gain insight into the performance of all components to quickly resolve any issues
- Installation and configuration: getting the product fully working and prepared for the end customer. Think of it as a car being delivered; getting it roadworthy
- Network: the way all the devices you use in your business are connected or connected to each other. Laptop on Wi-Fi, Wi-Fi with firewall, firewall with internet
- Reporting: putting on paper insights into network usage, component uptime and operation
- Security: securing your IT environment in the broadest sense of the word. Security includes all security and all security products that you use to protect your data from malicious and external parties who are not allowed to see the data
- Service level agreement: SLA; a clear agreement in which you agree the expectations between yourself and the IT vendor about what service you can expect. For example, how quickly your problems with IT are dealt with. Very convenient
- Wi-Fi surveying: measuring, creating and perfecting a survey of on-site Wi-Fi network coverage and performance
Modern Workplace
- Cloud: making your workspace available at any location. Being able to instantly access all your online files and data from anywhere. You can read more about how to go to the cloud here
- Collaborate efficiently: know where everything is by aggregating conversations, data and applications in one place. This makes collaboration a lot easier and more efficient
- Easy collaboration: Microsoft Teams was created by Microsoft, but is equally available for Apple. It doesn't matter what device or where you work. Someone working from a cafe on their MacBook can perfectly collaborate online with another person in the office
- Modern working: being able to perform your work independent of location or device. Microsoft Teams, servers, cloud services (Office 365, Azure) are part of this
- Collaborate securely: ensure availability, integrity and confidentiality of your data with one clear environment in the cloud. In a program like Microsoft Teams, you work in a secure environment
Security
- Backup: copy of your data, in case something goes wrong
- ISO 27001 certificate: certificate that we have, which verifies that we work securely. Hard to get and keep, so we are very proud of it
- LastPass: online application, as well as for on your PC and phone, that acts as a secure password vault
- Managed backup: a backup service fully managed by Lime Networks, guaranteeing security and proper operation
- MFA: multi factor authentication; an extra layer of security in that, for example, in addition to your password, you have to enter a code that you receive on your phone
- Phishing: form of Internet fraud in which cybercriminals try to steal your login credentials or information. They may also try to steal your credit card
- 'Secure by design': way of thinking where, whenever a product or service is chosen, the implication for the IT security of your environment is considered
- Spam: unwanted emails, from annoying newsletters to fake email
- Pentesting: testing to verify that your network and applications are secure
More on security
Telephony
- CDR: Call Detail Record; usage data such as call history, charges, usage or duration. Makes telephony transparent
- Extensions: internal connections to the telephone system, for example 201 to reach your colleague from marketing
- Hot-desking: the ability to log on to any phone with your own phone. You can say at your own desk: I want to be available now under number 03857372, and then everyone can reach you on that number. Work on any phone in your company or at home under your own account. You have that flexibility with us
- Number plan: ensures, for example, that Lime Networks' 010 number is linked across the entire help desk and therefore rings everywhere
- Operator: the portal where you operate your own telephony or let us handle it for you
- Reach: an app that lets you set up your extension
- Softphone: application that lets you make calls through your PC with a headset
- Telephony: a service package at Lime Networks where we take care of your telephony and take it off your hands
- Visual voicemail: easily see and listen to your voicemails on your mobile and on your screen
- VoIP: Voice over IP; voice over IP. A modern way of telephony over the Internet instead of over telephone cables
Does it go wrong? Then we are here for you!
Workplace management
- Antimalware: a program to stop malware.
- Antivirus: a program to stop viruses.
- Bitlocker: encrypting the storage in a PC/laptop so that theft of this does not mean loss of data
- EDR: the next step in antivirus/antimalware. Multiple systems controlled by Artificial Intelligence on your environment. EDR stops unknown infections and can limit damage
- Endpoint: a PC/laptop used by employees to perform work for the company
- Endpoint management: registering, securing, updating and automated maintenance of hardware, licenses, warranties, age and the user of a PC/laptop
- Hardware & software: everything for your workstation, servers, your network, security, Microsoft licenses or your conference room
- License management: managing all the purchased software you have
- Maintenance contracts: an agreement where we can guarantee that your IT always performs optimally. For your workstation, servers, network, or security, telephony or just endpoints
- Workplace: your workplace in the office, on the road or at home. Think of your PC/laptop, screen(s) and/or peripherals, but also your standard software and licenses
Projects and Migrations
- Projects: migrations, moves or a switch; we are here for you. We provide knowledge, experience and work with a fixed schedule. Projects always precede with a PVA and a Fixed-Price offer.
- Migration: a subcategory of projects, where there is a mutation to a component or an entire IT system is replaced
- PA: plan of action. Every project starts with the creation of a plan of action. This describes exactly what we will do in the intended project with clear steps, insight into risks responsibilities and the project team. A detailed inventory (often at the customer's location) provides a roadmap based on established facts. This plan also provides input for a fixed price offer without surprises.
- Quote: clear understanding of the cost of a project. Clearly divided into steps and cost items as described in the PVA. Almost all our quotations are fixed price unless otherwise indicated and discussed in person.
Example cases
From servers to Azure
- Azure: the set of cloud services from Microsoft. This is about renting servers, databases, storage, AI, IOT and hundreds of different things to move all your IT services in the background to the cloud
- CAPEX: CAPital EXpenses; an expenditure that you make in 1 lump sum rather than spread over several months or years
- Digital transformation: modernizing your IT environment so employees can use more software and hardware when they need it
- Hosting services: registration, management and security of domains and all traffic about them (DNS records)
- Hybrid cloud: own servers in a secure data center. Per month without investment supplemented with cloud services and continuity. More efficient than the cloud and delivers higher performance
- OPEX: OPerational EXpenses; depreciation over a longer period of time making it easier to incur large expenditures
- Servers: a device that provides either services or data to your network
Partners in IT
- Customer engagement: customer engagement; in the field of IT, it involves a company acting proactively, really thinking with the customer and making processes transparent
- MSP: Managed Services Provider; a company that delivers managed, turnkey IT products and services to clients. That way you don't have to worry about it anymore!
- QBR: Quarterly Business Review; when we take a quarterly look at the status of goals, roadmap, requirements and other progress regarding a project
- TBR: Time-based Business Review; a strategy and consulting session that is not fixed to a specific time, but depends on what is needed. So this varies by company and purpose. For small companies, once every six months may suffice, while for larger companies it should be every two months. This ensures optimal efficiency
- vCIO: virtual Chief Information Officer; an external IT director/manager who will join you. Someone who knows how you can achieve better results in IT
- XLA: eXperience Level Agreement; the quality of the solution, i.e. how you experienced the solution offered and the entire process
That's it, all the tricky, often misunderstood IT terms listed by IT service. At Lime Networks, we take care of our customers and will always explain IT terms in our communications. This is how we make complex IT simple. If you have any questions, please contact us at 010-2121806 | info@limenetworks.nl.